 |
 |
 |
 |
 |
|
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
|
| Braindump2go | Testking | Pass4sure | Actualtests | Others | |
| $99.99 | $124.99 | $125.99 | $189 | $29.99/$49.99 | |
| Up-to-Dated | ✔ | ✖ | ✖ | ✖ | ✖ |
| Real Questions | ✔ | ✖ | ✖ | ✖ | ✖ |
| Error Correction | ✔ | ✖ | ✖ | ✖ | ✖ |
| Printable PDF | ✔ | ✖ | ✖ | ✖ | ✖ |
| Premium VCE | ✔ | ✖ | ✖ | ✖ | ✖ |
| VCE Simulator | ✔ | ✖ | ✖ | ✖ | ✖ |
| One Time Purchase | ✔ | ✖ | ✖ | ✖ | ✖ |
| Instant Download | ✔ | ✖ | ✖ | ✖ | ✖ |
| Unlimited Install | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Pass Guarantee | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Money Back | ✔ | ✖ | ✖ | ✖ | ✖ |
[New 70-398 Dumps]Free Microsoft 79Q 70-398 Exam Dumps VCE and PDF Braindump2go Offer[42-52]
2018/August Braindump2go New Microsoft 70-398 Exam Dumps with PDF and VCE Free Updated Today! Following are some new 70-398 Real Exam Questions:
1.|2018 Latest 70-398 Exam Dumps (PDF & VCE) 79Q&As Download:
https://www.braindump2go.com/70-398.html
2.|2018 Latest 70-398 Exam Questions & Answers Download:
https://drive.google.com/drive/folders/0B75b5xYLjSSNSzdxYTQ2Z1FmRU0?usp=sharing
QUESTION 42
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
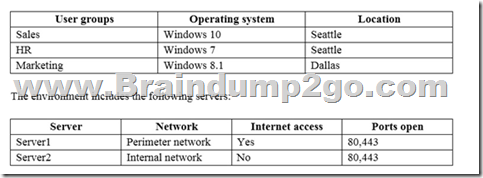
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
You need to view the events that you monitored for Marketing users.
Which log file should you view?
A. StatusAgent Log
B. System Event Log
C. Security Event Log
D. PolicyAgent Log
E. Application Event Log
Answer: C
Explanation:
https://docs.microsoft.com/en-us/windows/device-security/auditing/view-the-security-event-log
QUESTION 43
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
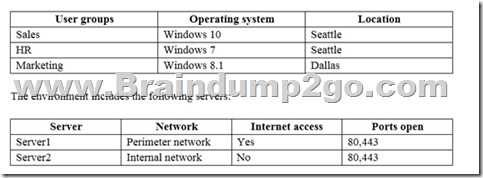
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
You need to configure synchronization.
Which option should you use?
A. the IdFix tool
B. Azure Active Directory Connect
C. Forefront Identity Manager 2010 R2
D. the Azure Active Directory Synchronization tool
E. the Directory Synchronization tool
Answer: B
QUESTION 44
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
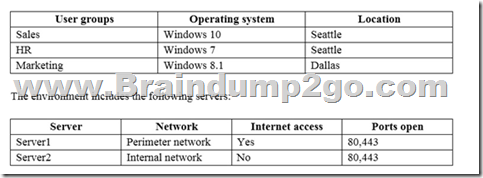
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to recover the file for the Sales department user in Seattle.
What should you do?
A. Run the following Windows PowerShell cmdlet: Start-WssServerFileRestore
B. Restore files from the Recycle Bin.
C. At a command prompt, run the following command: vssadmin.exe
D. Run the following Windows PowerShell cmdlet: Get-WBFileSpec
E. Restore files by using the File History applet.
F. At a command prompt, run the following command: recover.exe
Answer: E
Explanation:
https://support.microsoft.com/en-us/help/17143/windows-10-back-up-your-files
QUESTION 45
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
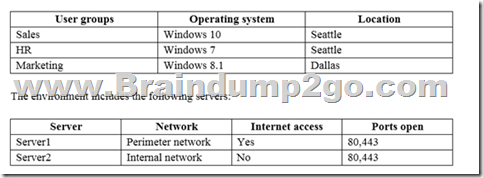
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
Hotspot Question
You need to implement the password requirements for the Office 365 portal.
Which three actions should you perform? To answer, select the appropriate option from each list in the answer area.
NOTE: Each correct selection is worth one point.
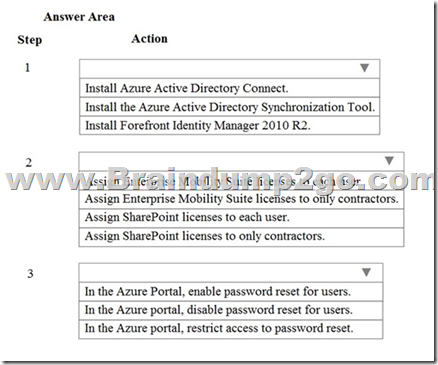
Answer:
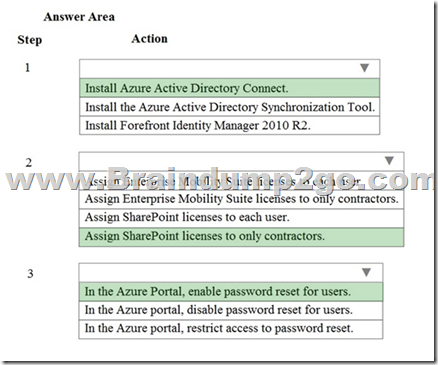
Explanation:
https://technet.microsoft.com/en-us/library/office-365-user-account-management.aspx
QUESTION 46
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
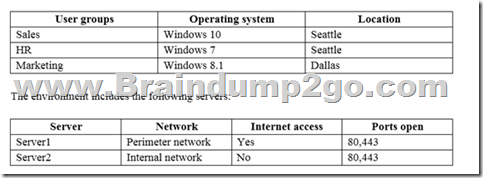
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
Hotspot Question
You need to recover the file for User1.
What should you do? To answer, select the appropriate option from each list in the answer area.
NOTE: Each correct selection is worth one point.
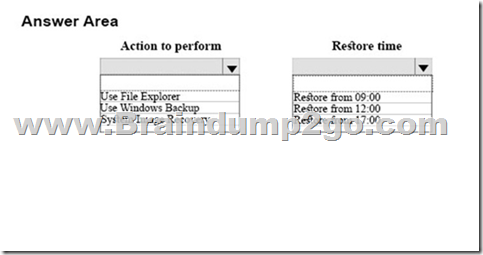
Answer:
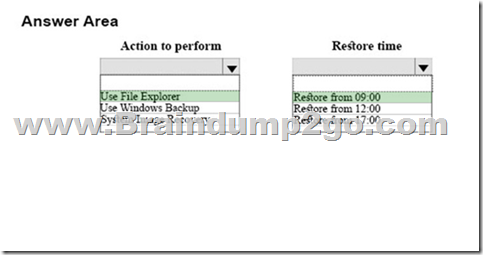
Explanation:
https://support.microsoft.com/en-us/help/17119/windows-7-recover-lost-deleted-files
QUESTION 47
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an on-premises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365 environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365 environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must be able to fully access local attached tape drives. Sales users must be prevented from writing to removable drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day on Monday through Friday.
All devices that run Windows 10 must back up the C:\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application. You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing applications or files.
Hotspot Question
You need to resolve the issues for the various groups of users.
Which recovery options should you use? To answer, select the appropriate option from each list in the answer area.
NOTE: Each correct selection is worth one point.
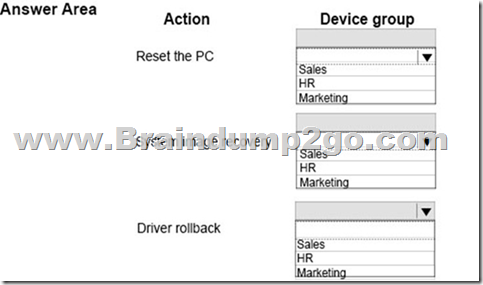
Answer: 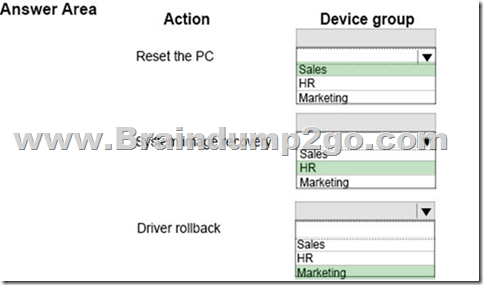
QUESTION 48
Overview
Background
Blue Yonder Airlines provides regional commercial jet services in the continental United States. The company also designs, manufactures, and sells custom parts for jet aircraft. The custom parts business is growing rapidly. Blue Yonder airlines has developed a new part that will help airlines comply with new safety regulations. The company has a backlog of customers that would like to purchase the part.
The Sales department has 500 users and the Engineering department has 200 users. All employees work eight hour shifts. The Sales and Engineering teams cannot effectively collaborate on projects. This has resulted in missed deadlines for releasing new products to manufacturing.
Mobile device management
Blue Yonder Airlines has a subscription to Microsoft Intune for Mobile Device Management (MDM). The subscription includes the MDM Authority and Terms and Conditions components. The company has deployed the Network Device Enrollment service, Enterprise Certification Authority, and the Intune Certificate Connector. Blue Yonder Airlines has an on-premises Microsoft Exchange environment.
The company will use a combination of Intune and Azure RemoteApp for Mobile Application Management.
Mobile devices for employees
Blue Yonder Airlines plans to deploy mobile devices to the Sales and Engineering department employees for use while they are outside of the company network. The company plans to deploy the latest iOS devices for Sales department users and Windows 10 tablet devices for Engineering department users.
You configure a Sales group for Sales department users and an Engineering group for Engineering department users. In Intune, you configure a computer device group for Windows 10 devices, and a mobile device group for iOS devices. You synchronize the Sales and Engineering groups with Azure Active Directory (AD).
Network resources
You have a network file share that is used by Engineering department users to collaborate on projects. The file share is configured with full control permissions. The company is concerned that users may be disrupted if they are suddenly denied access to the file share.
Applications
Inventory Management App
Blue Yonder Airlines has developed a custom inventory management app. Sales department users must be able to access the app from enrolled mobile devices. The data that the app uses is considered confidential and must be encrypted.
New product Sales App
You procure a third-party app from a vendor to support new product sales. The data that the app uses is highly confidential. You must restrict access to the app and the app’s data to only Engineering department users. The app has been signed by using a Blue Airlines certificate. This certificate is not trusted by devices that run Windows 10.
Product Request Program App
The company has developed the Product Request Program app as a 32-bit Windows application. The application allows the company to manage the sales fulfillment process. It is also used to record customer requests for new parts and services. You plan to publish the Product Request Program app in Azure RemoteApp and configure access for users in the Engineering and Sales departments. This app is not compatible with the iOS platform and cannot by published by using Intune. You create a virtual machine in Azure that runs Windows Server 2012 R2. You install the Product Request Program app on the virtual machine.
Business Requirements
You must ensure that the Sales and Engineering teams can share documents and collaborate effectively. Any collaboration solution must be highly available and must be accessible from the internet. You must restrict access to any shared files to prevent access.
You must restrict permissions to the Engineering file share. You must monitor access to the file share.
You must provide users in the Sales and Engineering departments access to the following resources:
Corporate email
File Shares hosted in Microsoft SharePoint Online
The Product Request Program app
Technical Requirements
You have the following technical requirements:
Allow all Sales department users to enroll iOS devices for device
management andenable encrypted notifications to the devices.
Employees must be able to access company resources without having to
manually install certificates or using an out-of-band process.
Employees must only access corporate resources from devices that
comply withthe company’s security policies.
Mobile device protection policies
All devices must include a trusted build and must comply with Blue
Yonder Airlines password complexity rules.
You must clear all corporate data from a mobile device when the number
of repeated log on failures is more than 10.
All devices must be protected from data loss in the event that a
device is lost or damaged.
Data that is considered confidential must be encrypted on devices.
Additional technical requirements for Engineering department users and devices
Users must not be challenged for credentials after they initially
enroll a device in Intune.
Users must be able to access corporate email on enrolled Windows 10
devices.
Devices must be automatically updated when an update is available. You
must configure the Intune agent to prompt for restart no more than one
time during normal business hours. System restarts to complete update
installations must occur outside of normal business hours.
Problem Statements
Sales and Engineering teams
Sales and Engineering department users report that it is difficult to share documents and collaborate on new projects. Blue Yonder Airlines has an urgent need to improve collaboration between the Sales department and Engineering department. Any collaboration solution must be highly available and accessible from the Internet.
Engineering department users report that Intune prompts them to restart their Windows 10 devices every 30 minutes when an update is available for installation. The prompts are disruptive to users.
Security issues
The Blue Yonder Airlines Security team has detected a vulnerability in Windows 10 devices. Microsoft has released a patch to address the vulnerability. The Security department has issued a service announcement. They request that you deploy the patch to all Windows 10 devices managed by Microsoft Intune.
Drag and Drop Question
You need to resolve the issue that engineering department users report regarding their Windows 10 devices.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
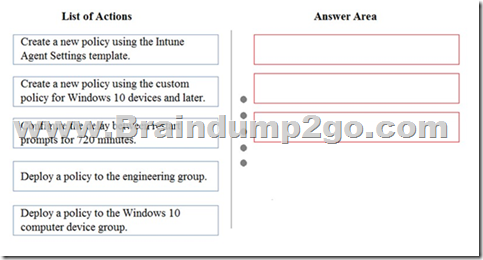
Answer:
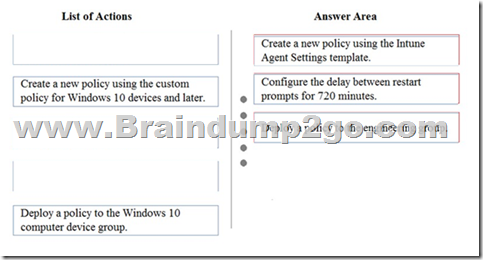
Explanation:
https://haukeberg.wordpress.com/2012/08/23/windows-intune-delayed-reboot-automatic-restart-restart-a-bit-later/
QUESTION 49
Overview
Background
Blue Yonder Airlines provides regional commercial jet services in the continental United States. The company also designs, manufactures, and sells custom parts for jet aircraft. The custom parts business is growing rapidly. Blue Yonder airlines has developed a new part that will help airlines comply with new safety regulations. The company has a backlog of customers that would like to purchase the part.
The Sales department has 500 users and the Engineering department has 200 users. All employees work eight hour shifts. The Sales and Engineering teams cannot effectively collaborate on projects. This has resulted in missed deadlines for releasing new products to manufacturing.
Mobile device management
Blue Yonder Airlines has a subscription to Microsoft Intune for Mobile Device Management (MDM). The subscription includes the MDM Authority and Terms and Conditions components. The company has deployed the Network Device Enrollment service, Enterprise Certification Authority, and the Intune Certificate Connector. Blue Yonder Airlines has an on-premises Microsoft Exchange environment.
The company will use a combination of Intune and Azure RemoteApp for Mobile Application Management.
Mobile devices for employees
Blue Yonder Airlines plans to deploy mobile devices to the Sales and Engineering department employees for use while they are outside of the company network. The company plans to deploy the latest iOS devices for Sales department users and Windows 10 tablet devices for Engineering department users.
You configure a Sales group for Sales department users and an Engineering group for Engineering department users. In Intune, you configure a computer device group for Windows 10 devices, and a mobile device group for iOS devices. You synchronize the Sales and Engineering groups with Azure Active Directory (AD).
Network resources
You have a network file share that is used by Engineering department users to collaborate on projects. The file share is configured with full control permissions. The company is concerned that users may be disrupted if they are suddenly denied access to the file share.
Applications
Inventory Management App
Blue Yonder Airlines has developed a custom inventory management app. Sales department users must be able to access the app from enrolled mobile devices. The data that the app uses is considered confidential and must be encrypted.
New product Sales App
You procure a third-party app from a vendor to support new product sales. The data that the app uses is highly confidential. You must restrict access to the app and the app’s data to only Engineering department users. The app has been signed by using a Blue Airlines certificate. This certificate is not trusted by devices that run Windows 10.
Product Request Program App
The company has developed the Product Request Program app as a 32-bit Windows application. The application allows the company to manage the sales fulfillment process. It is also used to record customer requests for new parts and services. You plan to publish the Product Request Program app in Azure RemoteApp and configure access for users in the Engineering and Sales departments. This app is not compatible with the iOS platform and cannot by published by using Intune. You create a virtual machine in Azure that runs Windows Server 2012 R2. You install the Product Request Program app on the virtual machine.
Business Requirements
You must ensure that the Sales and Engineering teams can share documents and collaborate effectively. Any collaboration solution must be highly available and must be accessible from the internet. You must restrict access to any shared files to prevent access.
You must restrict permissions to the Engineering file share. You must monitor access to the file share.
You must provide users in the Sales and Engineering departments access to the following resources:
Corporate email
File Shares hosted in Microsoft SharePoint Online
The Product Request Program app
Technical Requirements
You have the following technical requirements:
Allow all Sales department users to enroll iOS devices for device
management andenable encrypted notifications to the devices.
Employees must be able to access company resources without having to
manually install certificates or using an out-of-band process.
Employees must only access corporate resources from devices that
comply withthe company’s security policies.
Mobile device protection policies
All devices must include a trusted build and must comply with Blue
Yonder Airlines password complexity rules.
You must clear all corporate data from a mobile device when the number
of repeated log on failures is more than 10.
All devices must be protected from data loss in the event that a
device is lost or damaged.
Data that is considered confidential must be encrypted on devices.
Additional technical requirements for Engineering department users and devices
Users must not be challenged for credentials after they initially
enroll a device in Intune.
Users must be able to access corporate email on enrolled Windows 10
devices.
Devices must be automatically updated when an update is available. You
must configure the Intune agent to prompt for restart no more than one
time during normal business hours. System restarts to complete update
installations must occur outside of normal business hours.
Problem Statements
Sales and Engineering teams
Sales and Engineering department users report that it is difficult to share documents and collaborate on new projects. Blue Yonder Airlines has an urgent need to improve collaboration between the Sales department and Engineering department. Any collaboration solution must be highly available and accessible from the Internet.
Engineering department users report that Intune prompts them to restart their Windows 10 devices every 30 minutes when an update is available for installation. The prompts are disruptive to users.
Security issues
The Blue Yonder Airlines Security team has detected a vulnerability in Windows 10 devices. Microsoft has released a patch to address the vulnerability. The Security department has issued a service announcement. They request that you deploy the patch to all Windows 10 devices managed by Microsoft Intune.
Drag and Drop Question
You need to resolve the Security team service announcement.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
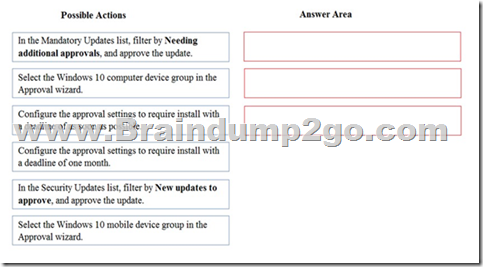
Answer:
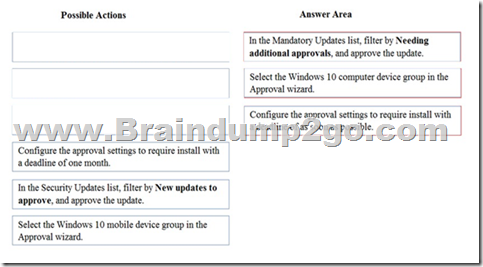
Explanation:
https://www.credera.com/blog/infrastructure/understanding-windows-updates-for-pcs-with-microsoft-intune/
QUESTION 50
Overview
Background
Fabrikam, Inc. is a large health services provider that serves the greater Chicago area. The company has three major hospital campus locations and over 30 individual care clinincs. Fabrikam has 4,000 employees. Doctors and nurses work in various locations and use shared kiosk workstations. Approximately, 1,000 employees are Information workers that use desktop or laptop computers. All users have their own Active Directory user accounts and Exchange mailboxes. Fabrikam has developed a software-as-a-service application Support app. Support technicians will use the app to resolve issues with medical equipment more quickly.
User log in to a Remote Desktop farm that is a member of the global fabrikam.com Active Directory Domain Services (AD DS) domain. All servers in the farm run Windows 2008 R2. Users access a set of line of business apps. They also access personal and departmental files that are located on network file shares by using Microsoft Office 2010 Standard.
Users at larger clinics work from company-owned devices that are connected to the global.fabrikam.com AD DS domain over private Wide Area Network links. At smaller clinics, users must connect to the Fabrikam network by using a shared internet connection from either their laptop or a shared workstation.
When users travel to smaller clinics or access the Fabrikam network remotely, they must use a Windows virtual private network (VPN) connection. Connections are made to a Windows 2008 R2 Server named RAS01, which hosts the Routing & Remote Access and Network Policy Services roles. These users are members of the Remote Users group, and must carry a two-factor token device and enter a six digit rotating pin when they connect. When they are not connected to the VPN and wish to use existing services, such as Microsoft Outlook on the Web, you must implement additional pre-authentication through Microsoft Threat Management Gateway.
All Internet traffic for user and server traffic runs through an access management system. Outbound traffic from the network to the internet must be explicitly granted access. Fabrikam uses System Center Configuration Manager (SCCM) on HTTPS mode to manage computers. All computers have a certificate from the Windows Private Key Infrastructure.
Mobile devices
Fabrikam has purchased 500 Apple ios devices. The company plans to issue these devices to doctors and nurses so that they can access apps and files from both inside and outside of the network. The company plans to deploy Microsoft Intune to manage laptop computers and mobile devices.
Business Requirements
Leadership needs
Company executives have identified the following requirements:
– You must minimize the workload for Information Technology teams and reduce operating costs.
– Target migration of applications towards a Software as a Service model.
– Empower users to work more efficiently no matter what location they are working from.
– Allow users to use modern devices.
– Secure mobile devices and operating environments.
– All communications must remain secure.
Information technology
You must implement features from both Microsoft Office 365 and Enterprise Mobility + Security to improve user productivity and reduce staff workloads.
Employees must use existing Active Directory credentials across on-premises and cloud solutions.
You must replace the line of business applications with cloud-based applications Reduce infrastructure costs by eliminating as many on-premises physical/virtual services as possible.
Secure data moving in and out of the organization.
Implement modern remote connectivity methods.
Technical requirements
Identity
You must enforce the following identity requirements:
– Deploy federated identity by using Microsoft Azure Active Directory Connect.
– Configure Federation Services to support workplace join.
– Monitor Federation Services health and report critical alerts to specific users.
– Ensure that any reverse proxy solution is capable of providing pre-authentication and two-factor authentication.
– You must populate the Azure App Panel with as many cloud-ready applications as possible.
– You must implement Azure Active Directory Premium as the preferred self-service password reset solution.
– You must use Azure Multi-Factor authentication as the preferred two-factor authentication solution.
Security
You have the following security requirements:
– Implement self-service password management.
– Use a minimum of three authentication methods for self-service password reset.
– Use AD DS security groups to control access to cloud-based applications.
– Integrate Azure Multi-Factor Authentication with existing platforms that support two-factor authentication.
– Use Azure Rights Management to secure company files and email that are transmitted outside of the network.
Other
You identify the following additional technical requirements:
– All users that operate in shared work spaces must use Windows to Go with Bittlocker.
– Windows to Go devices must automatically connect to the network by using DirectAccess.
– Remote connections to the network must use two-factor authentication.
– All laptop computers must be able to act as a mobile hotspot.
The network administrator for Fabrikam has asked you to assist in configuring Azure Active Directory (AD) Connect Health.
You need to recommend the prerequisite actions necessary to meet requirements.
Which three steps should you recommend? Each correct answer presents part of the solution. (Choose three.)
A. Configure audit policies on the Azure Active Directory Connect server.
B. Install agents on the Active Directory Federation Services server and the Web Application Proxy servers.
C. Configure firewall port and service connection exceptions.
D. Configure audit policies on both the Active Directory Federation Services (AS FS) server and the Web Application Proxy server.
E. Install an agent on the Azure Active Directory Connect server.
F. Configure Internet Explorer Enhanced Security allowed websites.
Answer: BCF
Explanation:
https://docs.microsoft.com/en-us/azure/active-directory/connect-health/active-directory-aadconnect-health-agent-install
QUESTION 51
Overview
Background
Fabrikam, Inc. is a large health services provider that serves the greater Chicago area. The company has three major hospital campus locations and over 30 individual care clinincs. Fabrikam has 4,000 employees. Doctors and nurses work in various locations and use shared kiosk workstations. Approximately, 1,000 employees are Information workers that use desktop or laptop computers. All users have their own Active Directory user accounts and Exchange mailboxes. Fabrikam has developed a software-as-a-service application Support app. Support technicians will use the app to resolve issues with medical equipment more quickly.
User log in to a Remote Desktop farm that is a member of the global fabrikam.com Active Directory Domain Services (AD DS) domain. All servers in the farm run Windows 2008 R2. Users access a set of line of business apps. They also access personal and departmental files that are located on network file shares by using Microsoft Office 2010 Standard.
Users at larger clinics work from company-owned devices that are connected to the global.fabrikam.com AD DS domain over private Wide Area Network links. At smaller clinics, users must connect to the Fabrikam network by using a shared internet connection from either their laptop or a shared workstation.
When users travel to smaller clinics or access the Fabrikam network remotely, they must use a Windows virtual private network (VPN) connection. Connections are made to a Windows 2008 R2 Server named RAS01, which hosts the Routing & Remote Access and Network Policy Services roles. These users are members of the Remote Users group, and must carry a two-factor token device and enter a six digit rotating pin when they connect. When they are not connected to the VPN and wish to use existing services, such as Microsoft Outlook on the Web, you must implement additional pre-authentication through Microsoft Threat Management Gateway.
All Internet traffic for user and server traffic runs through an access management system. Outbound traffic from the network to the internet must be explicitly granted access. Fabrikam uses System Center Configuration Manager (SCCM) on HTTPS mode to manage computers. All computers have a certificate from the Windows Private Key Infrastructure.
Mobile devices
Fabrikam has purchased 500 Apple ios devices. The company plans to issue these devices to doctors and nurses so that they can access apps and files from both inside and outside of the network. The company plans to deploy Microsoft Intune to manage laptop computers and mobile devices.
Business Requirements
Leadership needs
Company executives have identified the following requirements:
– You must minimize the workload for Information Technology teams and reduce operating costs.
– Target migration of applications towards a Software as a Service model.
– Empower users to work more efficiently no matter what location they are working from.
– Allow users to use modern devices.
– Secure mobile devices and operating environments.
– All communications must remain secure.
Information technology
You must implement features from both Microsoft Office 365 and Enterprise Mobility + Security to improve user productivity and reduce staff workloads.
Employees must use existing Active Directory credentials across on-premises and cloud solutions.
You must replace the line of business applications with cloud-based applications Reduce infrastructure costs by eliminating as many on-premises physical/virtual services as possible.
Secure data moving in and out of the organization.
Implement modern remote connectivity methods.
Technical requirements
Identity
You must enforce the following identity requirements:
– Deploy federated identity by using Microsoft Azure Active Directory Connect.
– Configure Federation Services to support workplace join.
– Monitor Federation Services health and report critical alerts to specific users.
– Ensure that any reverse proxy solution is capable of providing pre-authentication and two-factor authentication.
– You must populate the Azure App Panel with as many cloud-ready applications as possible.
– You must implement Azure Active Directory Premium as the preferred self-service password reset solution.
– You must use Azure Multi-Factor authentication as the preferred two-factor authentication solution.
Security
You have the following security requirements:
– Implement self-service password management.
– Use a minimum of three authentication methods for self-service password reset.
– Use AD DS security groups to control access to cloud-based applications.
– Integrate Azure Multi-Factor Authentication with existing platforms that support two-factor authentication.
– Use Azure Rights Management to secure company files and email that are transmitted outside of the network.
Other
You identify the following additional technical requirements:
– All users that operate in shared work spaces must use Windows to Go with Bittlocker.
– Windows to Go devices must automatically connect to the network by using DirectAccess.
– Remote connections to the network must use two-factor authentication.
– All laptop computers must be able to act as a mobile hotspot.
You need to recommend the security group for DirectAccess.
What should you recommend?
A. Use the existing Remote Users Active Directory security group. Add User accounts that require DirectAccess.
B. Use the existing Domain Computers Active Directory security group. Add Computer accounts that require DirectAccess.
C. Create a new Active Directory security group name Remote Computers. Add Computer accounts that require DirectAccess.
D. Create a new Active Directory security group name Remote Users. Add User accounts that require DirectAccess.
Answer: C
Explanation:
https://docs.microsoft.com/en-us/windows-server/remote/remote-access/directaccess/single-server-wizard/da-basic-configure-s1-infrastructure
QUESTION 52
Overview
Background
Fabrikam, Inc. is a large health services provider that serves the greater Chicago area. The company has three major hospital campus locations and over 30 individual care clinincs. Fabrikam has 4,000 employees. Doctors and nurses work in various locations and use shared kiosk workstations. Approximately, 1,000 employees are Information workers that use desktop or laptop computers. All users have their own Active Directory user accounts and Exchange mailboxes. Fabrikam has developed a software-as-a-service application Support app. Support technicians will use the app to resolve issues with medical equipment more quickly.
User log in to a Remote Desktop farm that is a member of the global fabrikam.com Active Directory Domain Services (AD DS) domain. All servers in the farm run Windows 2008 R2. Users access a set of line of business apps. They also access personal and departmental files that are located on network file shares by using Microsoft Office 2010 Standard.
Users at larger clinics work from company-owned devices that are connected to the global.fabrikam.com AD DS domain over private Wide Area Network links. At smaller clinics, users must connect to the Fabrikam network by using a shared internet connection from either their laptop or a shared workstation.
When users travel to smaller clinics or access the Fabrikam network remotely, they must use a Windows virtual private network (VPN) connection. Connections are made to a Windows 2008 R2 Server named RAS01, which hosts the Routing & Remote Access and Network Policy Services roles. These users are members of the Remote Users group, and must carry a two-factor token device and enter a six digit rotating pin when they connect. When they are not connected to the VPN and wish to use existing services, such as Microsoft Outlook on the Web, you must implement additional pre-authentication through Microsoft Threat Management Gateway.
All Internet traffic for user and server traffic runs through an access management system. Outbound traffic from the network to the internet must be explicitly granted access. Fabrikam uses System Center Configuration Manager (SCCM) on HTTPS mode to manage computers. All computers have a certificate from the Windows Private Key Infrastructure.
Mobile devices
Fabrikam has purchased 500 Apple ios devices. The company plans to issue these devices to doctors and nurses so that they can access apps and files from both inside and outside of the network. The company plans to deploy Microsoft Intune to manage laptop computers and mobile devices.
Business Requirements
Leadership needs
Company executives have identified the following requirements:
– You must minimize the workload for Information Technology teams and reduce operating costs.
– Target migration of applications towards a Software as a Service model.
– Empower users to work more efficiently no matter what location they are working from.
– Allow users to use modern devices.
– Secure mobile devices and operating environments.
– All communications must remain secure.
Information technology
You must implement features from both Microsoft Office 365 and Enterprise Mobility + Security to improve user productivity and reduce staff workloads.
Employees must use existing Active Directory credentials across on-premises and cloud solutions.
You must replace the line of business applications with cloud-based applications Reduce infrastructure costs by eliminating as many on-premises physical/virtual services as possible.
Secure data moving in and out of the organization.
Implement modern remote connectivity methods.
Technical requirements
Identity
You must enforce the following identity requirements:
– Deploy federated identity by using Microsoft Azure Active Directory Connect.
– Configure Federation Services to support workplace join.
– Monitor Federation Services health and report critical alerts to specific users.
– Ensure that any reverse proxy solution is capable of providing pre-authentication and two-factor authentication.
– You must populate the Azure App Panel with as many cloud-ready applications as possible.
– You must implement Azure Active Directory Premium as the preferred self-service password reset solution.
– You must use Azure Multi-Factor authentication as the preferred two-factor authentication solution.
Security
You have the following security requirements:
– Implement self-service password management.
– Use a minimum of three authentication methods for self-service password reset.
– Use AD DS security groups to control access to cloud-based applications.
– Integrate Azure Multi-Factor Authentication with existing platforms that support two-factor authentication.
– Use Azure Rights Management to secure company files and email that are transmitted outside of the network.
Other
You identify the following additional technical requirements:
– All users that operate in shared work spaces must use Windows to Go with Bittlocker.
– Windows to Go devices must automatically connect to the network by using DirectAccess.
– Remote connections to the network must use two-factor authentication.
– All laptop computers must be able to act as a mobile hotspot.
Hotspot Question
You need to configure the Azure Rights Management connector.
What should you do? To answer, select the appropriate action for each item in the answer area.
NOTE: Each correct selection is worth one point.
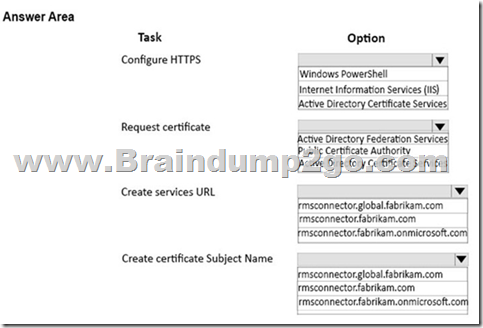
Answer:
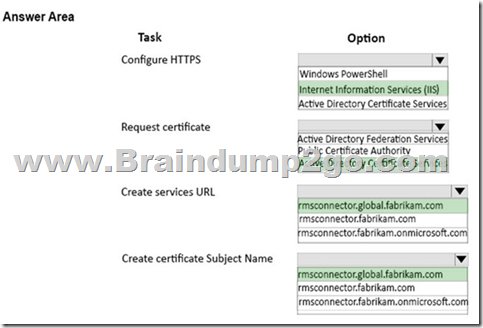
Explanation:
https://docs.microsoft.com/en-us/azure/information-protection/deploy-use/install-configure-rms-connector#configuring-the-rms-connector-to-use-https
!!!RECOMMEND!!!
1.|2018 Latest 70-398 Exam Dumps (PDF & VCE) 79Q&As Download:
https://www.braindump2go.com/70-398.html
2.|2018 Latest 70-398 Study Guide Video:
![[August-2019-New]Real AZ-100 PDF Dumps Free Download from Braindump2go(New Questions)](https://www.examsforalls.com/wp-content/themes/ribbon-lite/images/nothumb-related.png)