 |
 |
 |
 |
 |
|
|---|---|---|---|---|---|
 |
 |
 |
 |
 |
|
| Braindump2go | Testking | Pass4sure | Actualtests | Others | |
| $99.99 | $124.99 | $125.99 | $189 | $29.99/$49.99 | |
| Up-to-Dated | ✔ | ✖ | ✖ | ✖ | ✖ |
| Real Questions | ✔ | ✖ | ✖ | ✖ | ✖ |
| Error Correction | ✔ | ✖ | ✖ | ✖ | ✖ |
| Printable PDF | ✔ | ✖ | ✖ | ✖ | ✖ |
| Premium VCE | ✔ | ✖ | ✖ | ✖ | ✖ |
| VCE Simulator | ✔ | ✖ | ✖ | ✖ | ✖ |
| One Time Purchase | ✔ | ✖ | ✖ | ✖ | ✖ |
| Instant Download | ✔ | ✖ | ✖ | ✖ | ✖ |
| Unlimited Install | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Pass Guarantee | ✔ | ✖ | ✖ | ✖ | ✖ |
| 100% Money Back | ✔ | ✖ | ✖ | ✖ | ✖ |
[February-2023]High Quality Braindump2go 350-401 VCE and PDF 350-401 907Q Free Share[Q517-Q550]
February/2023 New Braindump2go 350-401 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 350-401 Real Exam Questions!
QUESTION 517
A network engineer must configure a router to send logging messages to a syslog server based on these requirements:
uses syslog IP address: 10.10.10.1
uses a reliable protocol
must not use any well-known TCP/UDP ports
Which configuration must be used?
A. logging host 10.10.10.1 transport tcp port 1024
B. logging origin-id 10.10.10.1
C. logging host 10.10.10.1 transport udp port 1023
D. logging host 10.10.10.1 transport udp port 1024
Answer: A
QUESTION 518
Refer to the exhibit. A network engineer must configure NETCONF. After creating the configuration, the engineer gets output from the command show line, but not from show running-config. Which command completes the configuration?

A. Device(config)# netconf max-sessions 100
B. Device(config)# no netconf ssh acl 1
C. Device(config)# netconf lock-time 500
D. Device(config)# netconf max-message 1000
Answer: D
Explanation:
Command: netconf max-message <1-2147483> Kbytes. The engineer gets output from the command show line, but not from show running-config, because max-message is too small, it is not enough for data of running-config.
QUESTION 519
An engineer is configuring a new SSID to present users with a splash page for authentication.
Which WLAN Layer 3 setting must be configured to provide this functionally?
A. CCKM
B. WPA2 Policy
C. Local Policy
D. Web Policy
Answer: D
Explanation:
https://www.cisco.com/c/en/us/support/docs/wireless/4400-series-wireless-lan-controllers/100787-splash-page-redirect.html
QUESTION 520
An engineer must create an EEM script to enable OSPF debugging in the event the OSPF neighborship goes down.
Which script must the engineer apply?
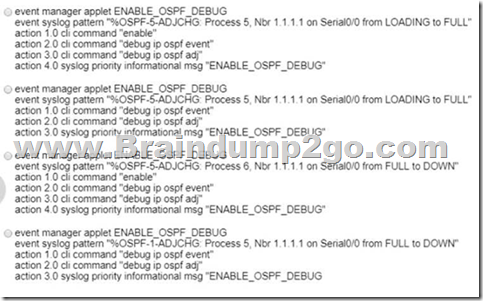
A. Option A
B. Option B
C. Option C
D. Option D
Answer: C
QUESTION 521
Refer to the exhibit. Router BRDR-1 is configured to receive the 0.0.0.0/0 and 172.17.1.0/24 networks via BGP and advertise them into OSPF area 0. An engineer has noticed that the OSPF domain is receiving only the 172.17.1.0/24 route and default route 0.0.0.0/0 is still missing. Which configuration must an engineer apply to resolve the problem?
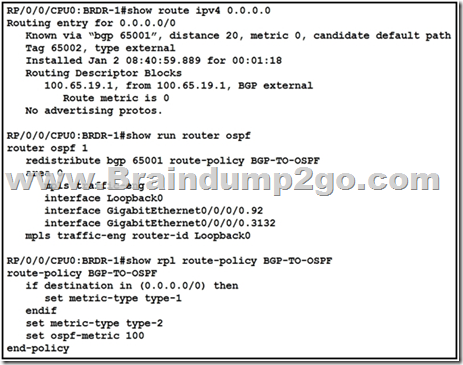
A. router ospf 1 redistribute bgp 65001 metric 100 route-policy BGP-TO-OSPF end
B. router ospf 1 default-information originate end
C. router ospf 1 default-metric 100 end
D. router ospf 1 default-information originate always end
Answer: D
QUESTION 522
AN engineer is implementing a route map to support redistribution within BGP. The route map must configured to permit all unmatched routes. Which action must the engineer perform to complete this task?
A. Include a permit statement as the first entry
B. Include at least one explicit deny statement
C. Remove the implicit deny entry
D. Include a permit statement as the last entry
Answer: D
QUESTION 523
Refer to the exhibit. A network operator is attempting to configure an IS-IS adjacency between two routers, but the adjacency cannot be established. To troubleshoot the problem, the operator collects this debugging output. Which interfaces are misconfigured on these routers?
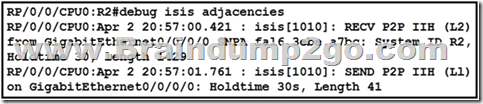
A. The peer router interface is configured as Level 1 only, and the R2 interface is configured as Level 2 only
B. The R2 interface is configured as Level 1 only, and the Peer router interface is configured as Level 2 only
C. The R2 interface is configured as point-to-point, and the peer router interface is configured as multipoint.
D. The peer router interface is configured as point-as-point, and the R2 interface is configured as multipoint.
Answer: B
QUESTION 524
AN engineer is implementing MPLS OAM to monitor traffic within the MPLS domain. Which action must the engineer perform to prevent from being forwarded beyond the service provider domain when the LSP is down?
A. Disable IP redirects only on outbound interfaces
B. Implement the destination address for the LSP echo request packet in the 127.x.y.z/8 network
C. Disable IP redirects on all ingress interfaces
D. Configure a private IP address as the destination address of the headend router of Cisco MPLS TE.
Answer: B
Explanation:
https://www.cisco.com/c/en/us/td/docs/routers/asr9000/software/asr9k-r7-5/mpls/configuration/guide/b-mpls-cg-asr9000-75x/implementing-mpls-oam-74x.html
QUESTION 525
An engineer is implementing a Cisco MPLS TE tunnel to improve the streaming experience for the clients of a video-on-demand server.
Which action must the engineer perform to configure extended discovery to support the MPLS LDP session between the headend and tailend routers?
A. Configure the interface bandwidth to handle TCP and UDP traffic between the LDP peers
B. Configure a Cisco MPLS TE tunnel on both ends of the session
C. Configure an access list on the interface to permit TCP and UDP traffic
D. Configure a targeted neighbor session.
Answer: B
QUESTION 526
What occurs when a high bandwidth multicast stream is sent over an MVPN using Cisco hardware?
A. The traffic uses the default MDT to transmit the data only if it isa (S,G) multicast route entry
B. A data MDT is created to if it is a (*, G) multicast route entries
C. A data and default MDT are created to flood the multicast stream out of all PIM-SM neighbors.
D. A data MDT is created to allow for the best transmission through the core for (S, G) multicast route entries.
Answer: D
QUESTION 527
Drag and Drop Question
An engineer is working with the Cisco DNA Center API Drag and drop the methods from the left onto the actions that they are used for on the right.
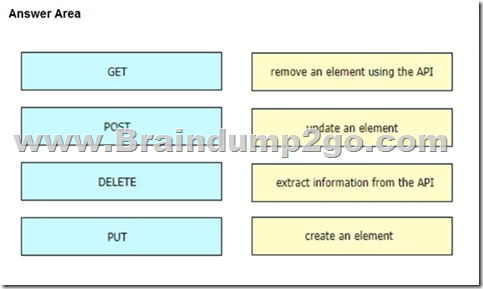
Answer:
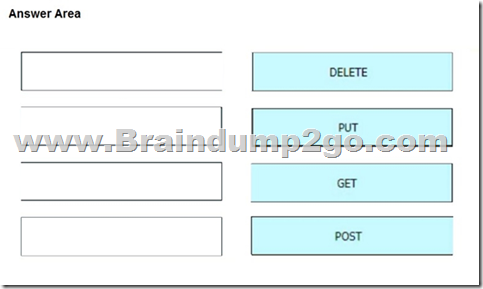
QUESTION 528
Drag and Drop Question
A network engineer is adding an additional 10Gps link to an exiting 2x10Gps LACP-based LAG to augment its capacity. Network standards require a bundle interface to be taken out of service if one of its member links goes down, and the new link must be added with minimal impact to the production network. Drag and drop the tasks that the engineer must perform from the left into the sequence on the right. Not all options are used.
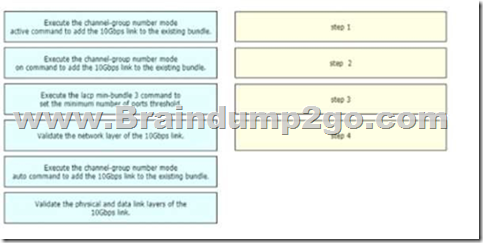
Answer:
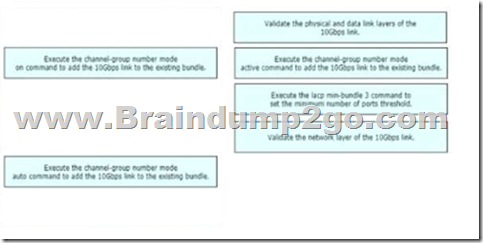
QUESTION 529
Which protocol is used to encrypt control plane traffic between SD-WAN controllers and SD-WAN endpoints?
A. DTLS
B. IPsec
C. PGP
D. HTTPS
Answer: A
QUESTION 530
An engineer must configure the strongest password authentication to locally authenticate on a router. Which configuration must be used?
A. username netadmin secret 5 $1$b1JUSkZbBS1Pyh4OzwXyZ1kSZ2
B. username netadmin secret $15b1JuSk404850110QzwXyZ1k SZ2
C. line Console 0
password $15b1Ju$
D. username netadmin secret 9 $9$vFpMfBelbRVV8SseX/bDAxtuV
Answer: D
Explanation:
Scrypt is safer than MD5, so answer A is wrong and answer D is correct
R1(config)#username user secret ?
0 Specifies an UNENCRYPTED secret will follow
5 Specifies a MD5 HASHED secret will follow
8 Specifies a PBKDF2 HASHED secret will follow
9 Specifies a SCRYPT HASHED secret will follow
< 0-9> Encryption types not explicitly specified
LINE The UNENCRYPTED (cleartext) user secret
LINE The UNENCRYPTED (cleartext) user secret
QUESTION 531
Which network devices secure API platform?
A. next-generation intrusion detection systems
B. Layer 3 transit network devices
C. content switches
D. web application firewalls
Answer: A
QUESTION 532
Which threat defence mechanism, when deployed at the network perimeter, protects against zero-day attacks?
A. intrusion prevention
B. stateful inspection
C. sandbox
D. SSL decryption
Answer: A
Explanation:
A zero-day (or 0-day) vulnerability is a software vulnerability that is discovered by attackers before the vendor has become aware of it. By definition, no patch exists for zero-day vulnerabilities and user systems have no defenses in place, making attacks highly likely to succeed. The name “zero-day” is designed to imply how long since the vulnerability was discovered. The term also indicates that system developers have had zero days to fix it.
Intrusion Protection
While the precise methods of a zero-day exploit can’t be known in advance, a network intrusion protection system (NIPS) can monitor the firms’ network for unusual activity.
The advantage of NIPS over a traditional antivirus only system is it does not rely on checking software against a known database of threats. This means it does not need updates or patches to learn about the latest attacks. NIPS works by monitoring the day-to-day patterns of network activity across the network.
When traffic or events far out of the ordinary are detected action can be taken to alert system administrators and lock down the firewall. Devices such as USB drives and mobile devices can all introduce threats to the network. They can often make it past the firewall because they are physically introduced to the system.
NIPS protects against threats introduced to the network from both external and internal sources.
Reference: https://cybriant.com/how-to-prevent-zero-day-attacks-in-5-steps/
QUESTION 533
Refer to the exhibit. A company requires that all wireless users authenticate using dynamic key generation.
Which configuration must be applied?
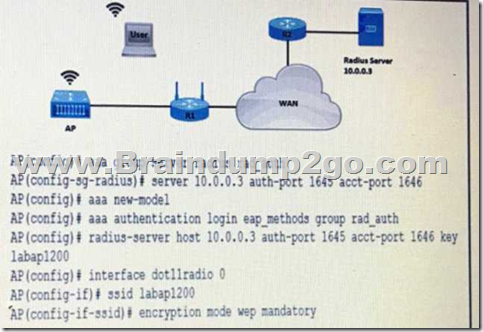
A. AP(config-if-ssid)# authentication open wep wep_methods
B. AP(config-if-ssid)# authentication dynamic wep wep_methods
C. AP(config-if-ssid)# authentication dynamic open wep_dynamic
D. AP(config-if-ssid)# authentication open eap eap_methods
Answer: D
QUESTION 534
An engineer is configuring a GRE tunnel interface in the default mode. The engineer has assigned an IPv4 address on the tunnel and sourced the tunnel from an Ethernet interface.
Which option also is required on the tunnel interface before it is operational?
A. (config-if)#tunnel destination <ip address>
B. (config-if)#keepalive <seconds retries>
C. (config-if)#ip mtu <value>
D. (config-if)#ip tcp adjust-mss <value>
Answer: A
QUESTION 535
What Is a Type 2 hypervisor?
A. installed as an application on an already installed operating system
B. runs directly on a physical server and includes its own operating system
C. supports over-allocation of physical resources
D. also referred to as a “bare metal hypervisor” because it sits directly on the physical server
Answer: A
QUESTION 536
Which two statements about static route configuration are true? (Choose two)
A. They add to the number of routes in the routing table.
B. The distance command modifies the administrative distance
C. The redistribute static command will redistribute classful networks into OSPF.
D. They add significant overhead to the router CPU.
E. The ip route static bfd command is used for BFD peer discovery.
F. The permanent key word allows the route to remain in the route table if the interface goes down.
Answer: CF
QUESTION 537
What is a characteristic of Cisco DNA Northbound APIs?
A. They simplify the management of network infrastructure devices.
B. They enable automation of network infrastructure based on intent.
C. They utilize RESTCONF.
D. They utilize multivendor support APIs.
Answer: B
Explanation:
Software-Defined Access (SDA) uses the software-defined architectural model, with a controller and various APIs. At the center sits the Digital Network Architecture (DNA) Center controller. DNA Center is the controller for SDA networks.
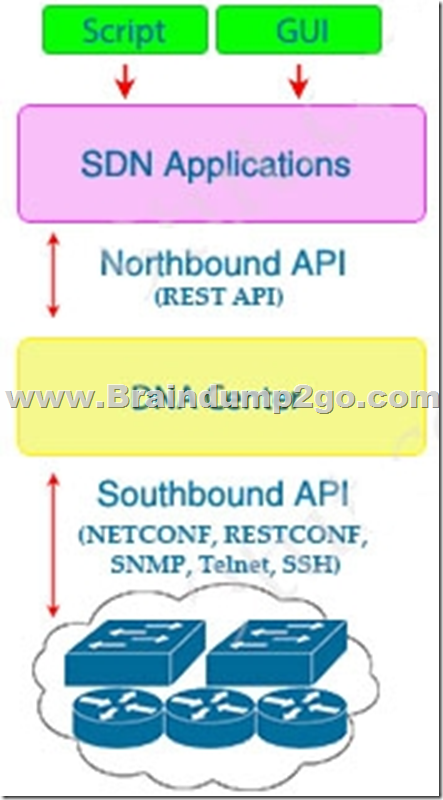
QUESTION 538
Which two items are found in YANG data models? (Choose two.)
A. HTTP return codes
B. rpc statements
C. JSON schema
D. container statements
E. XML schema
Answer: BE
QUESTION 539
What is required for a virtual machine to run?
A. a Type 1 hypervisor and a host operating system
B. a hypervisor and physical server hardware
C. only a Type 1 hypervisor
D. only a Type 2 hypervisor
Answer: B
QUESTION 540
An engineer configures GigabitEthernet 0/1 for VRRP group 115. The router must assume the primary role when it has the highest priority in the group.
Which command set is required to complete this task?
interface GigabitEthernet0/1
ip address 10.10.10.2 255.255.255.0
vrrp 115 ip 10.10.10.1
vrrp 115 authentication 407441579
A. Router(config if)# vrrp 115 track 1 decrement 100
Router(config-if)# vrrp 115 preempt
B. Router(config-if)# vrrp 115 track 1 decrement 10
Router(config-if)# vrrp 115 preempt
C. Router(config-if)# standby 115 priority 100
Router(config-if)# standby 115 preempt
D. Router(config-if)# vrrp 115 priority 100
Answer: B
QUESTION 541
An engineer must configure AAA on a Cisco 9800 WLC for central web authentication.
Which two commands are needed to accomplish this task? (Choose two.)
A. (Cisco Controller) > config wlan aaa-override disable <wlan-id>
B. (Cisco Controller) > config radius acct add 10.10.10.12 1812 SECRET
C. (Cisco Controller) > config wlan aaa-override enable <wlan-id>
D. Device(config-locsvr-da-radius)# client 10.10.10.12 server-key 0 SECRET
E. Device(config)# aaa server radius dynamic-author
Answer: DE
Explanation:
Answer A and answer C are used to enable/disable AAA Override option but it is just optional so they are not the correct answers. AAA Override enables you to apply VLAN tagging, Quality of Service, and Access Control Lists to individual clients based on the returned RADIUS attributes from the AAA server.
According to this Cisco link (under AAA Configuration on 9800 WLCs) section, we need the following commands:
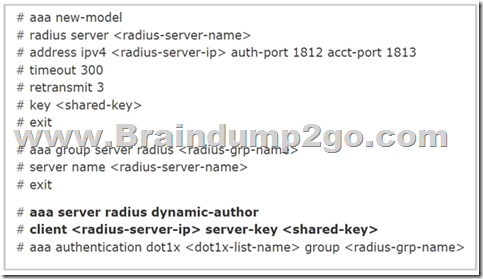
Therefore answer D and answer E are correct.
https://www.cisco.com/c/en/us/support/docs/wireless/catalyst-9800-series-wireless-controllers/213919-configure-802-1x-authentication-on-catal.pdf
QUESTION 542
What is a benefit of Type 1 hypervisors?
A. Administrators are able to load portable virtual machine packages in OVA or QCOW2 formats.
B. Network engineers are able to create virtual networks o interconnect virtual machines in Layer 2 topologies
C. Operators are able to leverage orchestrators to manage workloads that run on multiple Type 1 hypervisors
D. Storage engineers are able to leverage VMDK files to provide storage to virtual machine.
Answer: B
QUESTION 543
Refer to the exhibit. An engineer is troubleshooting an application running on Apple phones. The application Is receiving incorrect QoS markings. The systems administrator confirmed that ail configuration profiles are correct on the Apple devices.
Which change on the WLC optimizes QoS for these devices?
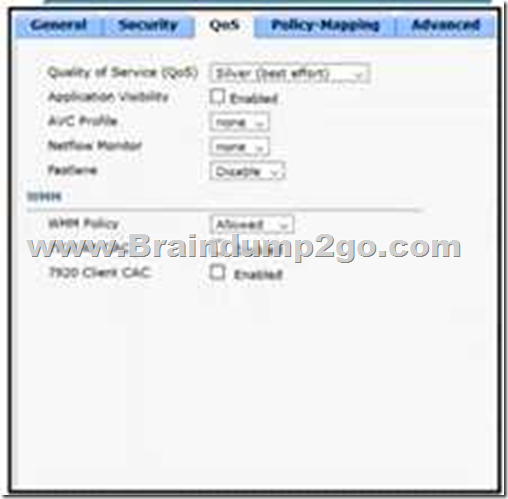
A. Enable Fastlane
B. Set WMM to required
C. Change the QoS level to Platinum
D. Configure AVC Profiles
Answer: A
Explanation:
Apple iOS device mark QoS as per IETF recommendations. With WLC running AireOS8.3, you can enable the Fastlane feature, which enables several beneficial functions:
– Your WLC QoS configuration is optimized globally to better support real-time applications
– iOS 10 devices can send upstream voice traffic without the requirement to perform WMM TSPEC/TCLAS negotiation. The infrastructure will honor the voice marking for these devices.
– You can apply a QoS profile to your iOS 10 devices, and decide which applications should receive QoS marking upstream, and which applications should be sent as best effort or background.
Reference: https://www.cisco.com/c/dam/en/us/td/docs/wireless/controller/technotes/8-3/Optimizing_WiFi_Connectivity_and_Prioritizing_Business_Apps.pdf
QUESTION 544
A client device roams between wireless LAN controllers that are mobility peers, Both controllers have dynamic interface on the same client VLAN which type of roam is described?
A. intra-VLAN
B. inter-controller
C. intra-controller
D. inter-subnet
Answer: B
Explanation:
Inter-controller Layer 2 roaming occurs when the wireless LAN interfaces of the controllers are on the same IP subnet.
QUESTION 545
Refer to the exhibit. Which result does the python code achieve?

A. The code encrypts a base64 decrypted password.
B. The code converts time to the “year/month/day” time format.
C. The code converts time to the yyyymmdd representation.
D. The code converts time to the Epoch LINUX time format.
Answer: C
QUESTION 546
Which technology uses network traffic telemetry, contextual information, and file reputation to provide insight into cyber threats?
A. threat defense
B. security services
C. security intelligence
D. segmentation
Answer: A
QUESTION 547
Drag and Drop Question
Drag and drop the characteristics from the left onto the deployment models on the right.

Answer:
QUESTION 548
Which two new security capabilities are introduced by using a next-generation firewall at the Internet edge? (Choose two.)
A. VPN
B. integrated intrusion prevention
C. application-level inspection
D. NAT
E. stateful packet inspection
Answer: BC
Explanation:
A next-generation firewall is a part of the third generation of firewall technology, combining a traditional firewall with other network device filtering functions, such as an application firewall using in-line deep packet inspection, an intrusion prevention system.
QUESTION 549
Drag and Drop Question
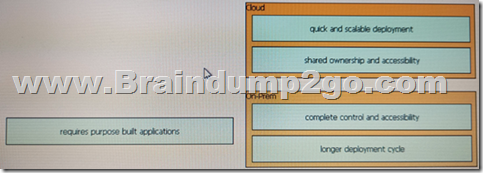
Drag and drop the characteristics from the left to the deployment models on the right. Not all options are used.
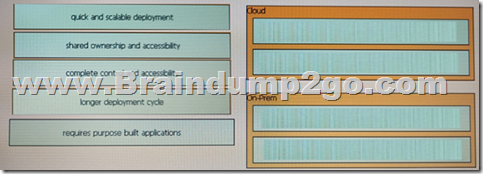
Answer:
QUESTION 550
Refer to the exhibit. A network engineer attempts to connect to the Router1 console port.
Which configuration is needed to allow Telnet connections?
A. Router1(config)# line vty 0 15
Router1(config-line)# transport output telnet
B. Router1(config)# telnet client
C. Router1(config)# line console 0
Router1(config-line)# transport output telnet
D. Router1(config)# access-list 100 permit tcp any any eq telnet
Router1(config)# line console 0
Router1(config-line)# access-class 100 out
Answer: C
Resources From:
1.2023 Latest Braindump2go 350-401 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/350-401.html
2.2023 Latest Braindump2go 350-401 PDF and 350-401 VCE Dumps Free Share:
https://drive.google.com/drive/folders/1EIsykNTrKvqjDVs9JMySv052qbrCpe8V?usp=sharing
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
![[July-2018-New]Valid Braindump2go 200-105 PDF Dumps and 200-105 VCE Dumps 539Q Offer[122-135]](https://www.examsforalls.com/wp-content/themes/ribbon-lite/images/nothumb-related.png)